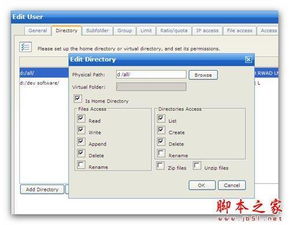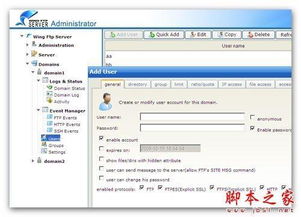
In today's digital age, the importance of using secure software cannot be overstated. With the increasing number of cyber threats and data breaches, it is crucial for individuals and organizations to adopt best practices in software usage to protect their sensitive information. This article aims to provide an overview of secure software usage, highlighting key considerations and best practices.
Secure software refers to applications that are designed with security in mind, ensuring that they are resistant to attacks and vulnerabilities. This includes both the software itself and the processes involved in its development, deployment, and maintenance. Secure software is built to protect user data, maintain system integrity, and ensure compliance with relevant regulations.
When using secure software, there are several key considerations to keep in mind:
Authentication and Authorization: Ensure that the software employs strong authentication methods to verify the identity of users and that proper authorization controls are in place to restrict access to sensitive data.
Encryption: Use encryption to protect data both in transit and at rest. This ensures that even if data is intercepted or accessed by unauthorized parties, it remains unreadable.
Regular Updates and Patch Management: Keep the software up to date with the latest security patches and updates to address any known vulnerabilities.
Secure Coding Practices: Developers should follow secure coding practices to minimize the introduction of vulnerabilities during the software development process.
User Education: Educate users about the importance of secure software usage, including the risks of phishing attacks, malware, and other cyber threats.
Here are some best practices to enhance the security of software usage:
Use Strong Passwords: Create strong, unique passwords for each account and consider using a password manager to securely store them.
Enable Multi-Factor Authentication (MFA): MFA adds an additional layer of security by requiring users to provide two or more forms of verification before accessing an account.
Keep Software Updated: Regularly update all software, including operating systems, browsers, and applications, to ensure that the latest security patches are applied.
Use Antivirus and Anti-Malware Software: Install reputable antivirus and anti-malware software to detect and prevent malicious software from infecting your system.
Be Wary of Phishing Attempts: Be cautious of unsolicited emails, messages, or calls asking for personal information. Always verify the legitimacy of the request before providing any sensitive data.
Backup Data Regularly: Regularly backup important data to an external location or cloud storage to prevent data loss in the event of a cyber attack.
Selecting secure software is essential for maintaining a secure computing environment. Here are some tips for choosing secure software:
Research and Evaluate: Research the software's security features, reputation, and user reviews before making a decision.
Check for Certifications: Look for certifications such as ISO 27001, which demonstrate that the software has been independently assessed for its security controls.
Review the Vendor's Security Policy: Ensure that the vendor has a robust security policy in place to protect your data and address any potential vulnerabilities.
Consider Open Source Alternatives: Open source software can be a good option, as the source code is publicly available for review and scrutiny.
Secure software usage is a critical component of maintaining a safe and secure digital environment. By understanding the importance of secure software, following best practices, and choosing the right software solutions, individuals and organizations can significantly reduce their risk of falling victim to cyber threats and data breaches.